Support Approved in Endpoint Privilege Management
- Sam Vokes

- May 20, 2024
- 3 min read
Introduction
Intune Service 2403 saw the release of Support Approved in Endpoint Privilege management.
Endpoint Privilege Management, included in Intune Suite, allows standard users to run supported applications with elevated administrative privileges without requiring a local administrator account or role on the device. EPM helps reduce the risk of cyberattacks and lateral movement by implementing the principle of least privilege and only giving users elevated permission to applications and services they need to fulfil their role.
Support Approved is a new option available in EPM to allow chosen users to request elevation to run applications on their device, without requiring the application to be managed by an EPM rule.
Enabling Support Approved
Go to Microsoft Intune > Endpoint Security > Endpoint Privilege Management and create a new Elevation settings policy.
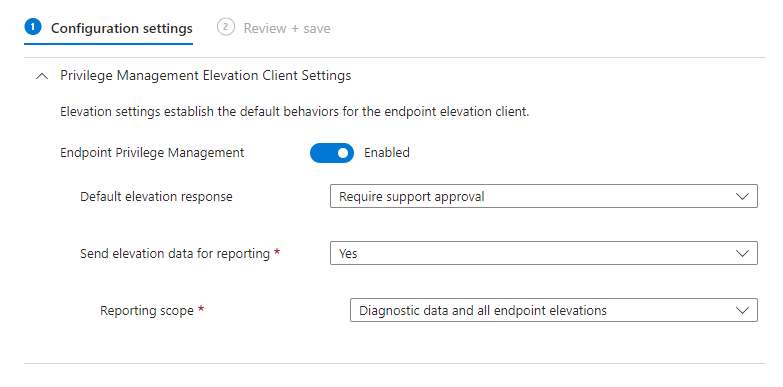
Assign this profile to your chosen users or devices.
Note: The default response for an elevation request would be applicable to any file that isn't managed by a EPM elevation rule policy. So be cautious changing your default response if you're in a production environment or deploying this to users/devices for the first time. You may not want supported approved as the default action to all of your EPM users.
Note: For Support Approved to work in the default elevation response, no rule can exist for the application AND an end user must explicitly request elevation through the Run with elevated access right-click menu.
Request: End User Experience
When the elevations settings policy is successfully deployed to the device. The user can right click on any supported application (.exe) and select Run with elevated access

The user enters their justification why they require elevation and presses send.

Support Approved Admin Experience
Support Approved requires an admin to approve all requests in Microsoft Intune. The following Intune RBAC roles are available without requiring an Intune Administrator role, Intune Administrator has the permission by default.

In Microsoft Intune > Endpoint Security > Endpoint Privilege Management > Elevation requests the approver will see a list of requests made by applicable users with request status' for each request.

For this example, we're interested in the latest Pending request for an application called Audacity.exe. The approver can see within this UI who has requested elevation under Username.
When clicking into the elevation request, the approver can see information about Compliance status, User justification (what the user entered during the request), and file hash value. This information should be useful when determining to approve or deny the request. So it's important an approver reads this information carefully. Additionally, this information could also be used to define an EPM rule for a particular user or groups of users.

If the approver selects approve, they must provide a reason why.

Approved: End User Experience
After 4-6 minutes the end user receives a toast notification from the Intune Management Extension advising the request has been approved.

Note: users do not receive a toast notification for denied requests. Slightly annoying.
A user must then right click Run with elevated access for the app that was requested and select Continue. The application will open with elevated rights for 24 hours.
Registry
If a request is approved, a new registry item is created in HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\EPMAgent\RuleLookup\FileName and will exist for 24 hours and automatically removed.

How the registry item is created is via a scheduled task using the the MMP-C (Declared Configuration) service: Support Approved | EPM | Endpoint Privilege Management (call4cloud.nl)




